This article will teach you how to encrypt data using EncFS on Ubuntu 22.04. Encryption is the process of converting data into a secret code that hides the true meaning of the data. Cryptography is the study of encrypting and decrypting information.
Unencrypted data is referred to as plaintext in computing, while encrypted data is referred to as ciphertext. Encryption algorithms, often known as ciphers, are formulas that are used to encode and decode messages.
EncFS is a cryptographic filesystem based on the Free FUSE operating system. It transparently encrypts files and stores the encrypted files in an arbitrary directory. Mounting an EncFS filesystem requires two directories, the source directory and the mountpoint directory.
How to Encrypt data using EncFS on Ubuntu 22.04
Install EncFS on Ubuntu 22.04
Run the command below to install EncFS
sudo apt -y install encfsOutput
Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: libtinyxml2-6a The following NEW packages will be installed: encfs libtinyxml2-6a 0 upgraded, 2 newly installed, 0 to remove and 4 not upgraded. Need to get 453 kB of archives. After this operation, 2,125 kB of additional disk space will be used. Get:1 http://us.archive.ubuntu.com/ubuntu focal/universe amd64 libtinyxml2-6a amd64 7.0.0+dfsg-1build1 [28.4 kB] Get:2 http://us.archive.ubuntu.com/ubuntu focal/universe amd64 encfs amd64 1.9.5-1build2 [425 kB] Fetched 453 kB in 3s (163 kB/s) Preconfiguring packages ... Selecting previously unselected package libtinyxml2-6a:amd64. (Reading database ... 245546 files and directories currently installed.) Preparing to unpack .../libtinyxml2-6a_7.0.0+dfsg-1build1_amd64.deb ... Unpacking libtinyxml2-6a:amd64 (7.0.0+dfsg-1build1) ... Selecting previously unselected package encfs. Preparing to unpack .../encfs_1.9.5-1build2_amd64.deb ... Unpacking encfs (1.9.5-1build2) ... Setting up libtinyxml2-6a:amd64 (7.0.0+dfsg-1build1) ... Setting up encfs (1.9.5-1build2) ... Processing triggers for man-db (2.9.1-1) ... Processing triggers for libc-bin (2.31-0ubuntu9.2) ...
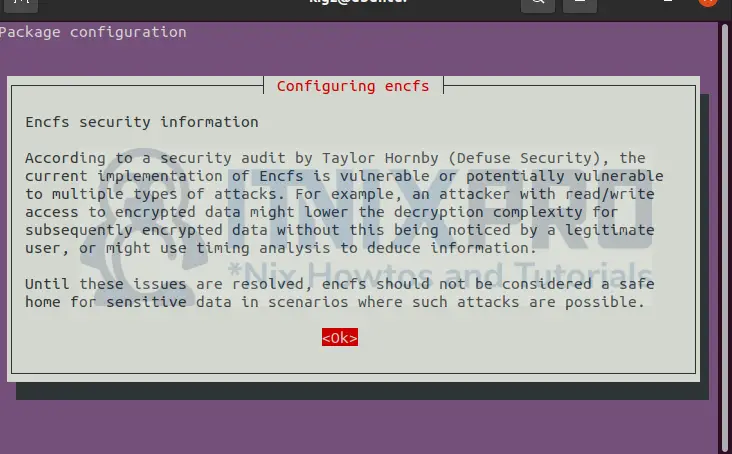
The screen below will pop saying you are not safe from attacks when using EncFS.
How to use EncFS on Ubuntu 22.04
Create an encrypted and decrypted directories in any location you desire. In my case, I’m going to create them in my home directory.
mkdir -p ~/encrypted
mkdir -p ~/decryptedThe mount point for the encrypted directory is the decrypted directory. Run the command below to mount /encrypted to /decrypted
encfs ~/encrypted ~/decryptedYou will be prompted to choose between expert or pre-configured paranoia mode. Enter letter p for pre-configured paranoia mode. Then enter password that you will use to decrypt the folder.
Output
Creating new encrypted volume. Please choose from one of the following options: enter "x" for expert configuration mode, enter "p" for pre-configured paranoia mode, anything else, or an empty line will select standard mode. ?> p Paranoia configuration selected. Configuration finished. The filesystem to be created has the following properties: Filesystem cipher: "ssl/aes", version 3:0:2 Filename encoding: "nameio/block", version 4:0:2 Key Size: 256 bits Block Size: 1024 bytes, including 8 byte MAC header Each file contains 8 byte header with unique IV data. Filenames encoded using IV chaining mode. File data IV is chained to filename IV. File holes passed through to ciphertext. -------------------------- WARNING -------------------------- The external initialization-vector chaining option has been enabled. This option disables the use of hard links on the filesystem. Without hard links, some programs may not work. The programs 'mutt' and 'procmail' are known to fail. For more information, please see the encfs mailing list. If you would like to choose another configuration setting, please press CTRL-C now to abort and start over. Now you will need to enter a password for your filesystem. You will need to remember this password, as there is absolutely no recovery mechanism. However, the password can be changed later using encfsctl. New Encfs Password: Verify Encfs Password:
Run the command below to find the EncFS volume.
mountOutput
sysfs on /sys type sysfs (rw,nosuid,nodev,noexec,relatime) proc on /proc type proc (rw,nosuid,nodev,noexec,relatime) udev on /dev type devtmpfs (rw,nosuid,noexec,relatime,size=4019168k,nr_inodes=1004792,mode=755,inode64) devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000) tmpfs on /run type tmpfs (rw,nosuid,nodev,noexec,relatime,size=810528k,mode=755,inode64) /dev/sda5 on / type ext4 (rw,relatime,errors=remount-ro) securityfs on /sys/kernel/security type securityfs (rw,nosuid,nodev,noexec,relatime) tmpfs on /dev/shm type tmpfs (rw,nosuid,nodev,inode64) tmpfs on /run/lock type tmpfs (rw,nosuid,nodev,noexec,relatime,size=5120k,inode64) tmpfs on /sys/fs/cgroup type tmpfs (ro,nosuid,nodev,noexec,mode=755,inode64) cgroup2 on /sys/fs/cgroup/unified type cgroup2 (rw,nosuid,nodev,noexec,relatime,nsdelegate) cgroup on /sys/fs/cgroup/systemd type cgroup (rw,nosuid,nodev,noexec,relatime,xattr,name=systemd) pstore on /sys/fs/pstore type pstore (rw,nosuid,nodev,noexec,relatime) none on /sys/fs/bpf type bpf (rw,nosuid,nodev,noexec,relatime,mode=700) cgroup on /sys/fs/cgroup/pids type cgroup (rw,nosuid,nodev,noexec,relatime,pids) cgroup on /sys/fs/cgroup/perf_event type cgroup (rw,nosuid,nodev,noexec,relatime,perf_event) cgroup on /sys/fs/cgroup/memory type cgroup (rw,nosuid,nodev,noexec,relatime,memory) cgroup on /sys/fs/cgroup/cpu,cpuacct type cgroup (rw,nosuid,nodev,noexec,relatime,cpu,cpuacct) cgroup on /sys/fs/cgroup/net_cls,net_prio type cgroup (rw,nosuid,nodev,noexec,relatime,net_cls,net_prio) cgroup on /sys/fs/cgroup/misc type cgroup (rw,nosuid,nodev,noexec,relatime,misc) cgroup on /sys/fs/cgroup/rdma type cgroup (rw,nosuid,nodev,noexec,relatime,rdma) cgroup on /sys/fs/cgroup/cpuset type cgroup (rw,nosuid,nodev,noexec,relatime,cpuset) cgroup on /sys/fs/cgroup/hugetlb type cgroup (rw,nosuid,nodev,noexec,relatime,hugetlb) cgroup on /sys/fs/cgroup/devices type cgroup (rw,nosuid,nodev,noexec,relatime,devices) cgroup on /sys/fs/cgroup/blkio type cgroup (rw,nosuid,nodev,noexec,relatime,blkio) cgroup on /sys/fs/cgroup/freezer type cgroup (rw,nosuid,nodev,noexec,relatime,freezer) systemd-1 on /proc/sys/fs/binfmt_misc type autofs (rw,relatime,fd=28,pgrp=1,timeout=0,minproto=5,maxproto=5,direct,pipe_ino=26325) mqueue on /dev/mqueue type mqueue (rw,nosuid,nodev,noexec,relatime) hugetlbfs on /dev/hugepages type hugetlbfs (rw,relatime,pagesize=2M) debugfs on /sys/kernel/debug type debugfs (rw,nosuid,nodev,noexec,relatime) tracefs on /sys/kernel/tracing type tracefs (rw,nosuid,nodev,noexec,relatime) /var/lib/snapd/snaps/bare_5.snap on /snap/bare/5 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core_11993.snap on /snap/core/11993 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core_12603.snap on /snap/core/12603 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core18_2253.snap on /snap/core18/2253 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core18_2284.snap on /snap/core18/2284 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core20_1270.snap on /snap/core20/1270 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/gnome-3-28-1804_161.snap on /snap/gnome-3-28-1804/161 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/gnome-3-34-1804_77.snap on /snap/gnome-3-34-1804/77 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/gnome-3-34-1804_72.snap on /snap/gnome-3-34-1804/72 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/gnome-3-38-2004_87.snap on /snap/gnome-3-38-2004/87 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/gtk-common-themes_1519.snap on /snap/gtk-common-themes/1519 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/core20_1328.snap on /snap/core20/1328 type squashfs (ro,nodev,relatime,x-gdu.hide) fusectl on /sys/fs/fuse/connections type fusectl (rw,nosuid,nodev,noexec,relatime) configfs on /sys/kernel/config type configfs (rw,nosuid,nodev,noexec,relatime) /var/lib/snapd/snaps/gtk-common-themes_1506.snap on /snap/gtk-common-themes/1506 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/snap-store_547.snap on /snap/snap-store/547 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/snapd_14295.snap on /snap/snapd/14295 type squashfs (ro,nodev,relatime,x-gdu.hide) vmware-vmblock on /run/vmblock-fuse type fuse.vmware-vmblock (rw,relatime,user_id=0,group_id=0,default_permissions,allow_other) /var/lib/snapd/snaps/snap-store_558.snap on /snap/snap-store/558 type squashfs (ro,nodev,relatime,x-gdu.hide) /var/lib/snapd/snaps/snapd_14549.snap on /snap/snapd/14549 type squashfs (ro,nodev,relatime,x-gdu.hide) /dev/sda1 on /boot/efi type vfat (rw,relatime,fmask=0077,dmask=0077,codepage=437,iocharset=iso8859-1,shortname=mixed,errors=remount-ro) tmpfs on /run/user/1000 type tmpfs (rw,nosuid,nodev,relatime,size=810524k,mode=700,uid=1000,gid=1000,inode64) gvfsd-fuse on /run/user/1000/gvfs type fuse.gvfsd-fuse (rw,nosuid,nodev,relatime,user_id=1000,group_id=1000) /dev/fuse on /run/user/1000/doc type fuse (rw,nosuid,nodev,relatime,user_id=1000,group_id=1000) tmpfs on /run/snapd/ns type tmpfs (rw,nosuid,nodev,noexec,relatime,size=810528k,mode=755,inode64) nsfs on /run/snapd/ns/snap-store.mnt type nsfs (rw) encfs on /home/kigz/decrypted type fuse.encfs (rw,nosuid,nodev,relatime,user_id=1000,group_id=1000,default_permissions)
For a quick overview of the available directories, run the command below.
df -hOutput
Filesystem Size Used Avail Use% Mounted on udev 3.9G 0 3.9G 0% /dev tmpfs 792M 1.9M 790M 1% /run /dev/sda5 15G 13G 945M 94% / tmpfs 3.9G 0 3.9G 0% /dev/shm tmpfs 5.0M 4.0K 5.0M 1% /run/lock tmpfs 3.9G 0 3.9G 0% /sys/fs/cgroup /dev/loop0 128K 128K 0 100% /snap/bare/5 /dev/loop1 100M 100M 0 100% /snap/core/11993 /dev/loop2 111M 111M 0 100% /snap/core/12603 /dev/loop3 56M 56M 0 100% /snap/core18/2253 /dev/loop4 56M 56M 0 100% /snap/core18/2284 /dev/loop5 62M 62M 0 100% /snap/core20/1270 /dev/loop7 165M 165M 0 100% /snap/gnome-3-28-1804/161 /dev/loop9 219M 219M 0 100% /snap/gnome-3-34-1804/77 /dev/loop8 219M 219M 0 100% /snap/gnome-3-34-1804/72 /dev/loop10 248M 248M 0 100% /snap/gnome-3-38-2004/87 /dev/loop11 66M 66M 0 100% /snap/gtk-common-themes/1519 /dev/loop6 62M 62M 0 100% /snap/core20/1328 /dev/loop12 63M 63M 0 100% /snap/gtk-common-themes/1506 /dev/loop14 51M 51M 0 100% /snap/snap-store/547 /dev/loop15 44M 44M 0 100% /snap/snapd/14295 /dev/loop13 55M 55M 0 100% /snap/snap-store/558 /dev/loop16 44M 44M 0 100% /snap/snapd/14549 /dev/sda1 511M 4.0K 511M 1% /boot/efi tmpfs 792M 64K 792M 1% /run/user/1000 encfs 15G 13G 945M 94% /home/kigz/decrypted
Put your data in the decrypted directory, just like you would a normal directory, to save it in encrypted form.
cd ~/decrypted
echo "hello from itnix" > foo
echo "hello from itnix" > bar
ln -s foo foo2When you check directory contents using the command below, you’ll notice that it’s not encrypted.
ls -lOutput
total 8 -rw-rw-r-- 1 kigz kigz 10 Feb 9 15:09 bar -rw-rw-r-- 1 kigz kigz 10 Feb 9 15:09 foo lrwxrwxrwx 1 kigz kigz 3 Feb 9 15:09 foo2 -> foo
You can check if the directory is in encryption format by running the command below.
cd ~/encrypted
ls -lOutput
total 8 -rw-rw-r-- 1 kigz kigz 26 Feb 9 15:09 ateUfxCJ7M6KjhgDoGRh6du2 -rw-rw-r-- 1 kigz kigz 26 Feb 9 15:09 ldzPCfCy7O7bUje6cEVwcULB lrwxrwxrwx 1 kigz kigz 24 Feb 9 15:09 Pu8H5MDfmIU,nzufTA-ppWJx -> ateUfxCJ7M6KjhgDoGRh6du2
Run the following command to unmount the encrypted drive.
cd
fusermount -u ~/decryptedCheck if it’s unmounted. Run
mountThen run
df -hOutput
Filesystem Size Used Avail Use% Mounted on udev 3.9G 0 3.9G 0% /dev tmpfs 792M 1.9M 790M 1% /run /dev/sda5 15G 13G 945M 94% / tmpfs 3.9G 0 3.9G 0% /dev/shm tmpfs 5.0M 4.0K 5.0M 1% /run/lock tmpfs 3.9G 0 3.9G 0% /sys/fs/cgroup /dev/loop0 128K 128K 0 100% /snap/bare/5 /dev/loop1 100M 100M 0 100% /snap/core/11993 /dev/loop2 111M 111M 0 100% /snap/core/12603 /dev/loop3 56M 56M 0 100% /snap/core18/2253 /dev/loop4 56M 56M 0 100% /snap/core18/2284 /dev/loop5 62M 62M 0 100% /snap/core20/1270 /dev/loop7 165M 165M 0 100% /snap/gnome-3-28-1804/161 /dev/loop9 219M 219M 0 100% /snap/gnome-3-34-1804/77 /dev/loop8 219M 219M 0 100% /snap/gnome-3-34-1804/72 /dev/loop10 248M 248M 0 100% /snap/gnome-3-38-2004/87 /dev/loop11 66M 66M 0 100% /snap/gtk-common-themes/1519 /dev/loop6 62M 62M 0 100% /snap/core20/1328 /dev/loop12 63M 63M 0 100% /snap/gtk-common-themes/1506 /dev/loop14 51M 51M 0 100% /snap/snap-store/547 /dev/loop15 44M 44M 0 100% /snap/snapd/14295 /dev/loop13 55M 55M 0 100% /snap/snap-store/558 /dev/loop16 44M 44M 0 100% /snap/snapd/14549 /dev/sda1 511M 4.0K 511M 1% /boot/efi tmpfs 792M 64K 792M 1% /run/user/1000
The Output above shows EncFS volume isn’t listed anymore. To remount it, run
encfs ~/encrypted ~/decryptedYou’ll be prompted to enter the password you set up previously. If you need to change your password, you can do so using the following command.
encfsctl passwd ~/encryptedOutput
Enter current Encfs password EncFS Password: Enter new Encfs password New Encfs Password: Verify Encfs Password: Volume Key successfully updated.
You can learn more about EncFS on the Linux man page or alternatively by running the following command
man encfsCongratulations you have reached the end of the article. You have learned how to Encrypt data using EncFS on Ubuntu 22.04.
Other Tutorials
Install WordPress with LEMP Stack on Ubuntu 22.04