In this tutorial, you will learn how to setup Nagios Passive Checks with NRDP. Nagios Remote Data Processor (NDRP) is a flexible data transport mechanism and processor for Nagios. NRDP can be implemented as a replacement for NSCA. It has the capability to poll the host and service checks and push the check results to the central Nagios server.
Setup Nagios Passive Checks with NRDP
In order to setup Nagios passive checks with NRDP, we will implement some kind of Nagios distributed monitoring.
Our deployment will be based on the architecture below shown in the image below;
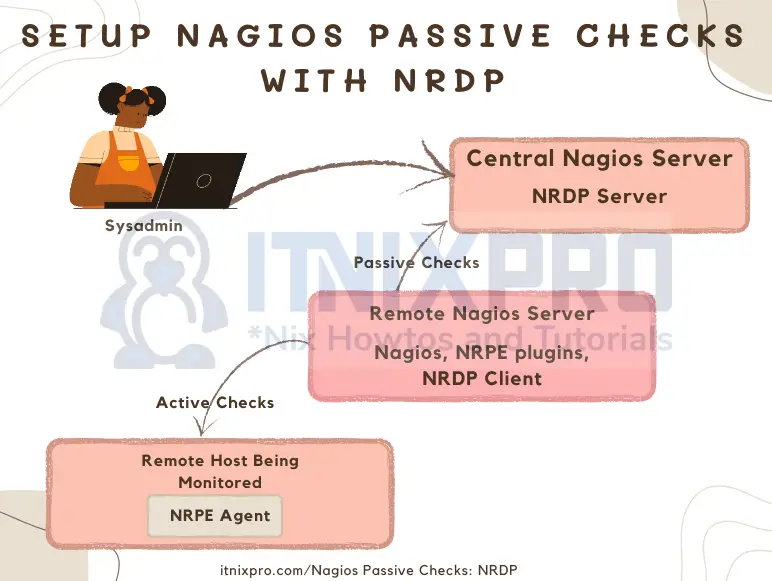
The are two setups of Nagios servers in this specific deployment;
- Central Nagios Server: In this context, the central Nagios server is a system sitting on a public network with a controlled access.
- Remote Nagios Server: In this context, the remote Nagios server is an internal system that is being used to monitor systems on Local LAN and can only be accessed on LAN.
There is no access to the remote Nagios server running in LAN. Thus, to ensure a visibility into the internal monitoring, passive checks of the internal systems via the remote Nagios server can be configured on the central Nagios server.
To ensure that the passive checks can be done on the central Nagios server, NRDP server and NRDP clients will be used.
NRDP server is deployed on the central Nagios server while NRDP client will be the internal Nagios server. Whenever a service or host check is done by the remote Nagios server, the results are read by the NRDP client and pushes them to the NRDP server. Once the NRDP server receives these checks, they are sent to central Nagios server which then displays and can be access from the web interface.
So, how can you setup passive Nagios checks? These are the steps;
- Install and setup central and Remote Nagios Servers.
- Create Passive Host and Service checks Templates on central Nagios server
- Configure SIMILAR host and service checks configuration on both Nagios servers. The names of hosts and service descriptions MUST match on both Nagios systems.
- Install and setup NRDP Server on Central Nagios Server
- Install NRDP Clients on Remote Nagios to Submit Check Results to Central Nagios Server
- Configure Global Host and Service Event Handlers on Remote Nagios Server
- Confirm and verify Nagios passive checks on Central Nagios server
Install and setup Central and Remote Nagios Servers
First of all, ensure that the remote/internal Nagios server is already setup and internal host/services are being monitored already.
In this example setup, we only have two hosts being monitored on the internal nagios server;
Hosts;
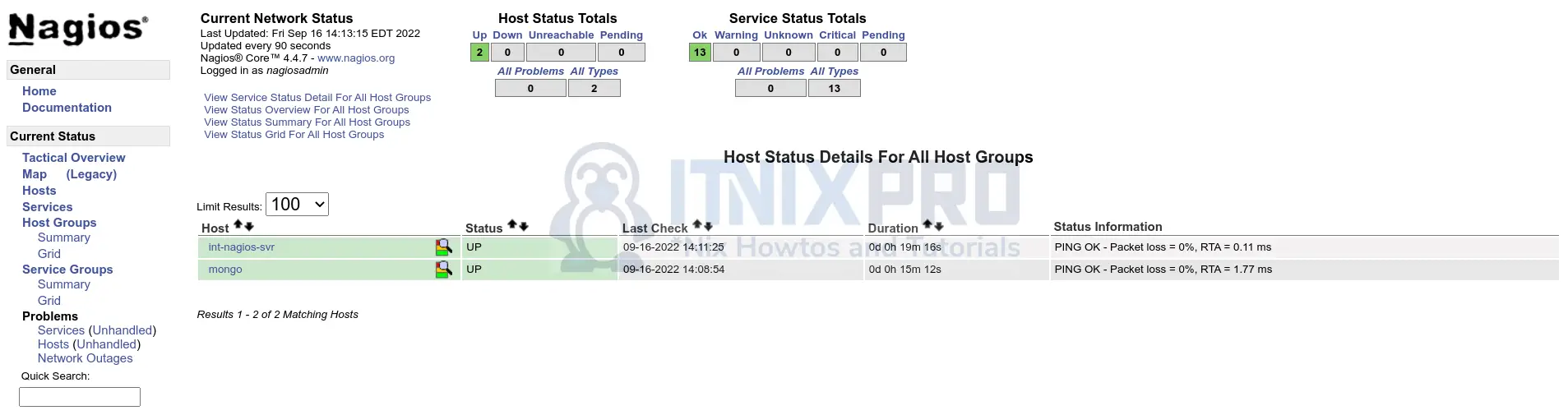
Services;
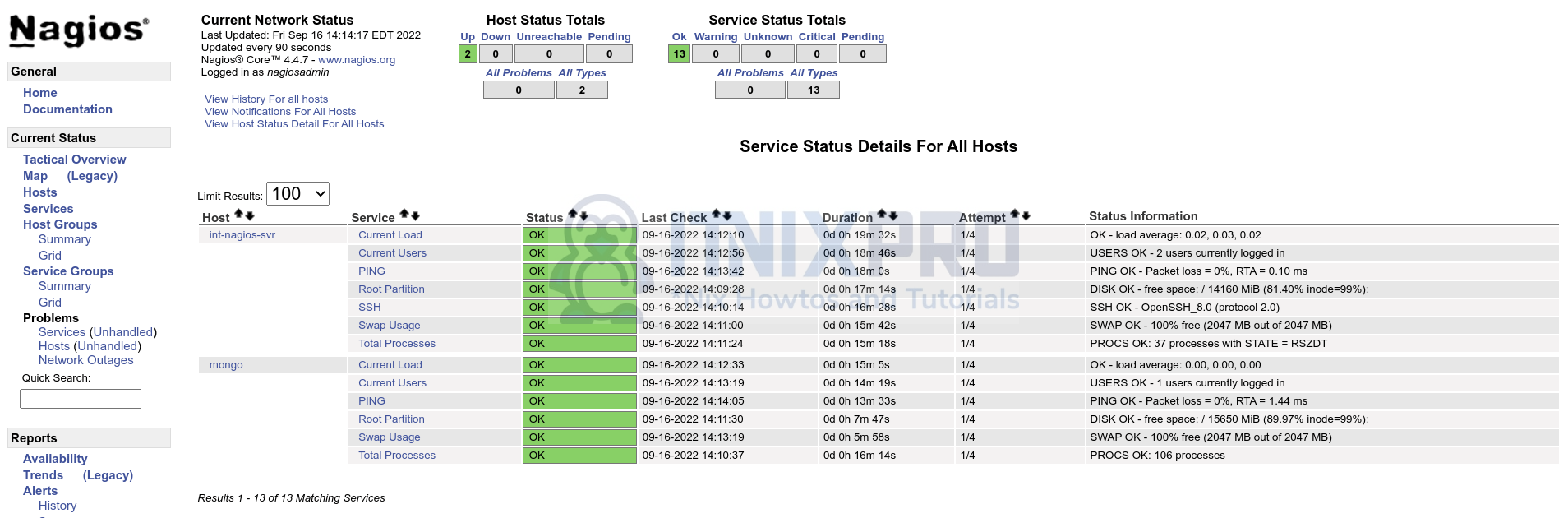
Next, install and setup central Nagios server. This is how our central nagios server looks like before passive checks is configured.
Hosts;
Services;
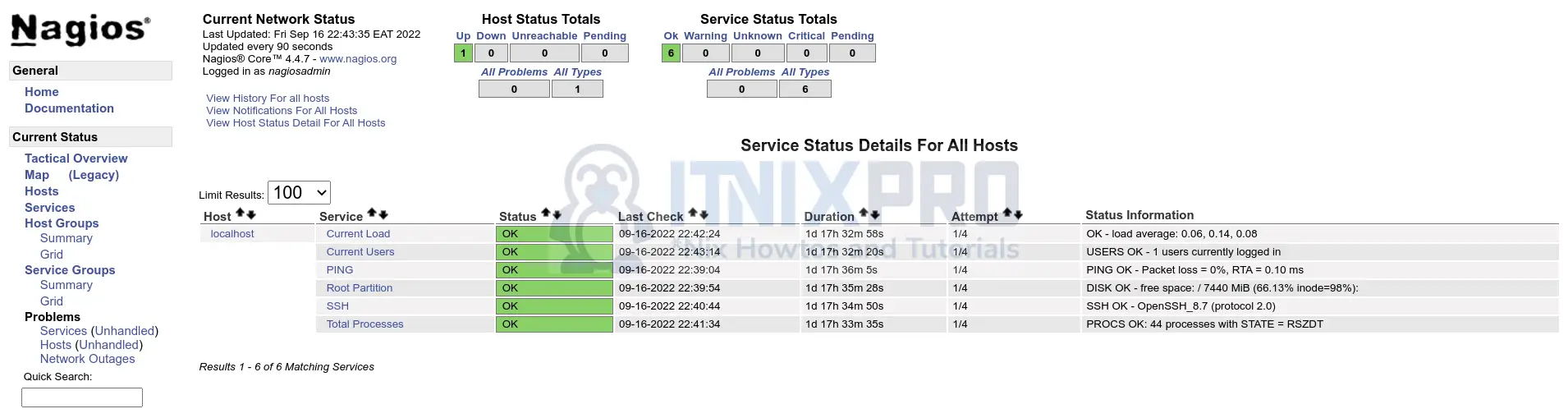
Create Passive Host and Service checks Templates on central Nagios server
On the central Nagios server, you need to define the Passive checks host and service templates.
This is what we have;
cat /usr/local/nagios/etc/objects/passive/host-service-template.cfg## Passive Checks Host and Service Templates
define host {
name passive_host
event_handler_enabled 1
active_checks_enabled 0
passive_checks_enabled 1
check_period 24x7
max_check_attempts 3
check_interval 5
retry_interval 2
register 0
}
define service {
name passive_service
register 0
max_check_attempts 3
check_interval 5
retry_interval 2
active_checks_enabled 0
passive_checks_enabled 1
notifications_enabled 1
check_period 24x7
check_command dummy_service_state
}
#
define command{
command_name dummy_service_state
command_line /usr/local/nagios/libexec/dummy_service_state.sh
}
If you can see the Service template, we have a check_command option. This defines the command (dummy_service_state) that Nagios will run in order to actively check the status of the service. However, we are only running passive checks on this central server. Hence, we use a command that executes a dummy script (/usr/local/nagios/libexec/dummy_service_state.sh) that will output unknownl status about the host.
The content of the script is shown below;
cat /usr/local/nagios/libexec/dummy_service_state.sh#!/bin/sh
/usr/bin/printf "UNKNOWN: Service State is Unknown\n"
exit 3chmod +x /usr/local/nagios/libexec/dummy_service_state.shAlso, if you noticed, we didnt define any contacts for these host/service definitions. If you want to enable notifications based on passive checks, then go ahead and do it.
Configure SIMILAR host and service descriptions on both Nagios servers
Next, ensure that host names and the service descriptions are same on both Nagios deployments.
For example, on our remote/internal Nagios server, these are the host and service definitions for the mongo system;
cat /usr/local/nagios/etc/objects/hosts-services.cfgdefine host {
use linux-server
host_name mongo
alias mongo
address 192.168.56.144
}
define service {
use local-service
host_name mongo
service_description PING
check_command check_ping!100.0,20%!500.0,60%
}
define service {
use local-service
host_name mongo
service_description Root Partition
check_command check_nrpe_disk!20%!10%!/
}
define service {
use local-service
host_name mongo
service_description Current Users
check_command check_nrpe_users!20!50
}
define service {
use local-service
host_name mongo
service_description Total Processes
check_command check_nrpe_procs!250!400!RSZDT
}
define service {
use local-service
host_name mongo
service_description Current Load
check_command check_nrpe_load!5.0,4.0,3.0!10.0,6.0,4.0
}
define service {
use local-service
host_name mongo
service_description Swap Usage
check_command check_nrpe_swap!20%!10%
}
From the above, you can see the host_name is mongo
All the services being monitored and their descriptions;
| Service | Description |
| Host State | PING |
| Host Disk Usage | Root Partition |
| Host Logged in Users | Current Users |
| Host No of Running Processes | Total Processes |
| Host Load Average | Current Load |
| Host Swap Memory Usage | Swap Usage |
On the central nagios server, these are the host and service definitions;
cat /usr/local/nagios/etc/objects/remote-hosts-services.cfg## Hosts Definitions
define host {
use passive_host
host_name mongo
alias mongo
}
# Service Definitions
define service {
use passive_service
host_name mongo
service_description PING
}
define service {
use passive_service
host_name mongo
service_description Root Partition
}
define service {
use passive_service
host_name mongo
service_description Current Users
}
define service {
use passive_service
host_name mongo
service_description Total Processes
}
define service {
use passive_service
host_name mongo
service_description Current Load
}
define service {
use passive_service
host_name mongo
service_description Swap Usage
}
The names of the hosts and service descriptions matches those on the remote/internal system.
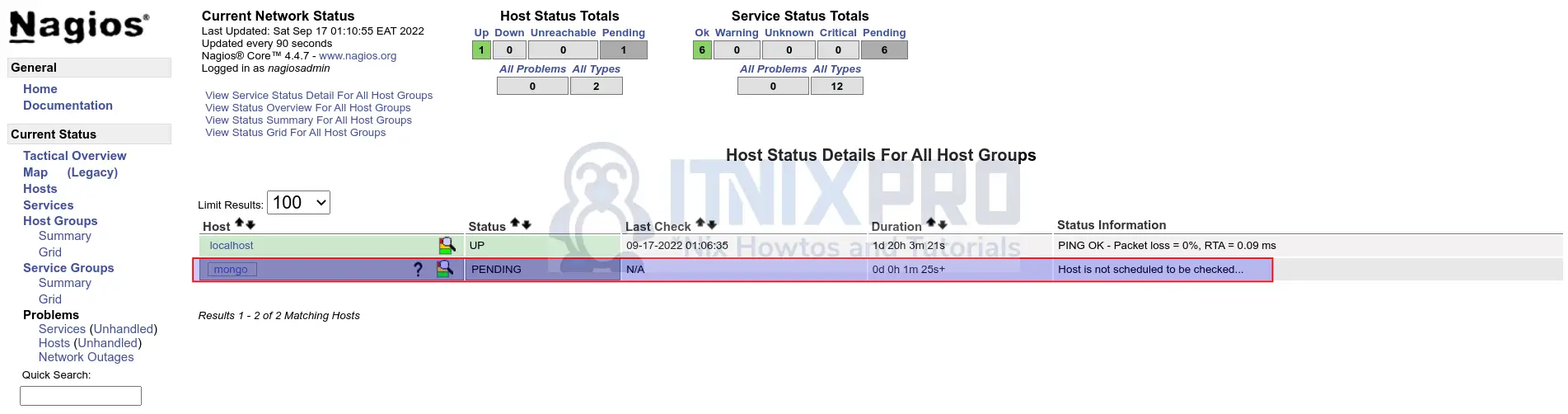
Restart Nagios service on the central server.
systemctl restart nagiosIf you navigate back to central Nagios server UI, you will see mongo host added alongside its respective services;
Hosts;
Services;
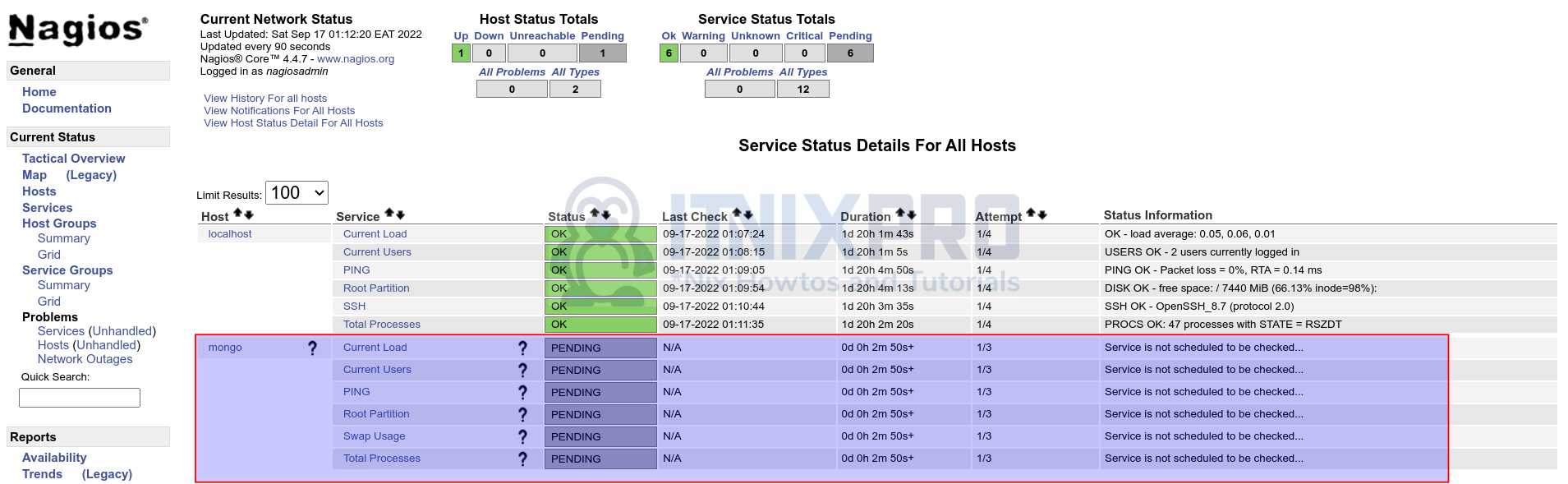
Install and Configure NRDP Server on Central Nagios Server
NRDP Server provides an API to which the NRDP client will send the host/service check results to from remote Nagios to a central Nagios server using the HTTP protocol. The API can be accessed via the url http[s]://<nagios-domain>/nrdp.
To install NRDP server on a central Nagios server, proceed as follow;
Install Required build tools.
If you are running Ubuntu/Debian;
sudo apt install php-xmlIf you are running CentOS/Rocky/Oracle/RHEL;
sudo yum install php-xml php-jsonDownload the current release NRDP source tarball from releases page;
wget -P /tmp https://github.com/NagiosEnterprises/nrdp/archive/refs/tags/2.0.5.tar.gzExtract and compile NRDP;
cd /tmptar xzf 2.0.5.tar.gzcd /tmp/nrdp-2.0.5/mkdir -p /usr/local/nrdp
cp -r clients server LICENSE* CHANGES* /usr/local/nrdp
chown -R nagios:nagios /usr/local/nrdp Next, define tokens to be used for communication between NRDP client and NRDP server API running on the central Nagios server;
vim /usr/local/nrdp/server/config.inc.php...
/////////////////////////////////////////////////////////////
//
// authorized_tokens
//
// An array of one or more tokens that are valid for this NRDP install
// a client request must contain a valid token in order for the NRDP to response or honor the request
// NOTE: Tokens are just alphanumeric strings - make them hard to guess!
$cfg["authorized_tokens"] = array(
// "mysecrettoken", // <-- not a good token
"90dfs7jwn3", // <-- a better token (don't use this exact one, make your own)
);
..
Next, copy the NRDP Apache configuration to Apache configurations directory.
On RHEL/Oracle/CentOS/Rocky;
cp /tmp/nrdp-2.0.5/nrdp.conf /etc/httpd/conf.d/On Ubuntu/Debian;
cp /tmp/nrdp-2.0.5/nrdp.conf /etc/apache2/sites-enabled/The NRDP API will be accessible via http[s]://<nagios-domain>/nrdp.
Restrict access to the API by defining which IPs are allowed to access;
cp /etc/httpd/conf.d/nrdp.conf /etc/httpd/conf.d/nrdp.conf.bakNote the use of Require ip 192.168.56.0/24 192.168.57.0/24 192.168.58.0/24, within the <RequireAny> </RequireAny> config section;
Alias /nrdp "/usr/local/nrdp/server"
<Directory "/usr/local/nrdp">
# SSLRequireSSL
Options None
AllowOverride None
<IfVersion >= 2.3>
<RequireAny>
Require ip 192.168.56.0/24 192.168.57.0/24 192.168.58.0/24
# AuthName "NRDP"
# AuthType Basic
# AuthUserFile /usr/local/nrdp/htpasswd.users
# Require valid-user
</RequireAny>
</IfVersion>
<IfVersion < 2.3>
Order allow,deny
Allow from all
# Order deny,allow
# Deny from all
# Allow from 127.0.0.1
# AuthName "NRDP"
# AuthType Basic
# AuthUserFile /usr/local/nrdp/htpasswd.users
# Require valid-user
</IfVersion>
</Directory>
You can as well enable basic authentication if you want.
Restart Apache Service;
systemctl restart httpdsystemctl restart apache2If you want to test your NRDP API, just navigate to the test page. The page allows you to submit either a command or one or more host and service checks to
Nagios.
Install NRDP Client Scripts on Remote Nagios to Submit Check Results to Central Nagios Server
There exists three different types of NRDP clients; PHP based script, Python based script and bash script.
ls -1 /usr/local/nrdp/clients/send_nrdp.php
send_nrdp.py
send_nrdp_py2.py
send_nrdp.shYou can choose which one to use to push the check results to NRDP server. Thus, copy them from the central Nagios Server to remote Nagios server;
scp -r /usr/local/nrdp/clients username@remote-nagios-server:In this example setup, we will use the bash script.
Thus, place the script under /opt directory on the remote Nagios server;
cp -r clients /optThis is how the NRDP client bash script looks like;
cat /opt/clients/send_nrdp.sh#!/bin/bash ############################################################################## # # # send_nrdp.sh - Send host/service checkresults to NRDP with XML # # # Copyright (c) 2008-2020 - Nagios Enterprises, LLC. All rights reserved. # Originally Authored: Scott Wilkerson ([email protected]) # # License: GNU General Public License version 3 # # # This program is free software: you can redistribute it and/or modify # it under the terms of the GNU General Public License as published by # the Free Software Foundation, either version 3 of the License, or # (at your option) any later version. # # This program is distributed in the hope that it will be useful, # but WITHOUT ANY WARRANTY; without even the implied warranty of # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the # GNU General Public License for more details. # # You should have received a copy of the GNU General Public License # along with this program. If not, see <https://www.gnu.org/licenses/>. # ############################################################################# # # 2019-06-19 Jake Omann # - Fixed issue with XML output formatting on some PHP versions # # 2017-09-25 Troy Lea aka BOX293 # - Fixed script not working with arguments when run as a cron job # or if being used as a nagios command like obsessive compulsive. # ... "if [ ! -t 0 ]" was the reason why. # # 2017-12-08 Jørgen van der Meulen (Conclusion Xforce) # - Fixed typo in NRDP abbreviation # ############################################################################# PROGNAME=$(basename $0) RELEASE="Revision 0.6.1" print_release() { echo "$RELEASE" } print_usage() { echo "" echo "$PROGNAME $RELEASE - Send NRDP script for Nagios" echo "" echo "Usage: send_nrdp.sh -u URL -t token [options]" echo "" echo "Usage: $PROGNAME -h display help" echo "" } print_help() { print_usage echo "" echo "This script is used to send NRDP data to a Nagios server" echo "" echo "Required:" echo " -u"," URL of NRDP server. Usually http://<IP_ADDRESS>/nrdp/" echo " -t"," Shared token. Must be the same token set in NRDP Server" echo "" echo "Options:" echo " Single Check:" echo " -H Host name" echo " -s Service description" echo " -S State" echo " -o Output" echo "" echo " STDIN:" echo " -d Delimiter (Optional, default -d \"\\t\")" echo " With only the required parameters $PROGNAME is capable of" echo " processing data piped to it either from a file or other" echo " process. By default, we use \t as the delimiter however this" echo " may be specified with the -d option data should be in the" echo " following formats one entry per line." echo " For Host checks:" echo " Hostname State Output" echo " For Service checks" echo " Hostname Servicedesc State Output" echo "" echo " File:" echo " -f /full/path/to/file" echo " This file will be sent to the NRDP server specified in -u" echo " The file should be an XML file in the following format" echo " ##################################################" echo "" echo " <?xml version='1.0'?>" echo " <checkresults>" echo " <checkresult type=\"host\" checktype=\"1\">" echo " <hostname>YOUR_HOSTNAME</hostname>" echo " <state>0</state>" echo " <output>OK|perfdata=1.00;5;10;0</output>" echo " </checkresult>" echo " <checkresult type=\"service\" checktype=\"1\">" echo " <hostname>YOUR_HOSTNAME</hostname>" echo " <servicename>YOUR_SERVICENAME</servicename>" echo " <state>0</state>" echo " <output>OK|perfdata=1.00;5;10;0</output>" echo " </checkresult>" echo " </checkresults>" echo " ##################################################" echo "" echo " Directory:" echo " -D /path/to/temp/dir" echo " This is a directory that contains XML files in the format" echo " above. Additionally, if the -d flag is specified, $PROGNAME" echo " will create temp files here if the server could not be reached." echo " On additional calls with the same -D path, if a connection to" echo " the server is successful, all temp files will be sent." exit 0 } send_data() { pdata="token=$token&cmd=submitcheck" if [ ! "x$curl" == "x" ];then if [[ -n $file ]]; then rslt=`curl -f --silent --insecure -d "$pdata" --data-urlencode "xml@$file" "$url/"` else pdata="$pdata&xml=$1" rslt=`curl -f --silent --insecure -d "$pdata" "$url/"` fi ret=$? else pdata="$pdata&xml=$1" rslt=`wget -q --no-check-certificate -O - --post-data="$pdata" "$url/"` ret=$? fi status=`echo $rslt | sed -n 's|.*<status>\(.*\)</status>.*|\1|p'` message=`echo $rslt | sed -n 's|.*<message>\(.*\)</message>.*|\1|p'` if [ $ret != 0 ];then echo "ERROR: could not connect to NRDP server at $url" # verify we are not processing the directory already and then write to the directory if [[ -z $2 && -n $directory ]]; then if [[ ! -d $directory ]];then mkdir -p "$directory" fi # This is where we write to the tmp directory echo "$xml" > "$(mktemp "$directory/nrdp.XXXXXX")" fi exit 1 fi if [ "$status" != "0" ];then # This means we couldn't connect to NRPD server echo "ERROR: The NRDP Server said $message" # verify we are not processing the directory already and then write to the directory if [[ -z $2 && -n $directory ]]; then if [[ ! -d $directory ]];then mkdir -p "$directory" fi # This is where we write to the tmp directory echo "$xml" > "$(mktemp "$directory/nrdp.XXXXXX")" fi exit 2 fi # If this was a directory call and was successful, remove the file if [[ -n $2 && $status = '0' ]]; then rm -f "$2" fi # If we weren't successful error if [ $ret != 0 ];then echo "exited with error "$ret exit $ret fi } # Parse parameters while getopts "u:t:H:s:S:o:f:d:c:D:hv" option do case $option in u) url=$OPTARG ;; t) token=$OPTARG ;; H) host=$OPTARG ;; s) service=$OPTARG ;; S) State=$OPTARG ;; o) output=$OPTARG ;; f) file=$OPTARG ;; d) delim=$OPTARG ;; c) checktype=$OPTARG ;; D) directory=$OPTARG ;; h) print_help 0;; v) print_release exit 0 ;; esac done if [ ! $checktype ]; then checktype=1 fi if [ ! $delim ]; then delim=`echo -e "\t"` fi if [ "x$url" == "x" -o "x$token" == "x" ] then echo "Usage: send_nrdp -u url -t token" exit 1 fi # detecting curl if [[ `which curl` =~ "/curl" ]] then curl=1; fi # detecting wget if we don't have curl if [[ `which wget` =~ "/wget" ]] then wget=1; fi if [[ ! $curl && ! $wget ]]; then echo "Either curl or wget are required to run $PROGNAME" exit 1 fi checkcount=0 if [ $host ]; then xml="" # we are not getting piped results if [ "$host" == "" ] || [ "$State" == "" ]; then echo "You must provide a host -H and State -S" exit 2 fi if [ "$service" != "" ]; then xml="$xml<checkresult type='service' checktype='$checktype'> <servicename>$service</servicename>" else xml="$xml<checkresult type='host' checktype='$checktype'>" fi # urlencode XML special chars output=${output//&/%26} output=${output//</%3C} output=${output//>/%3E} xml="$xml<hostname>$host</hostname> <state>$State</state> <output><![CDATA["$output"]]></output> </checkresult>" checkcount=1 fi # If only url and token have been provided then it is assumed that data is being piped ######################## if [[ ! $host && ! $State && ! $file && ! $directory ]]; then xml="" # we know we are being piped results IFS=$delim while read -r line ; do arr=($line) if [ ${#arr[@]} != 0 ];then if [[ ${#arr[@]} < 3 ]] || [[ ${#arr[@]} > 4 ]];then echo "ERROR: STDIN must be either 3 or 4 fields long, I found "${#arr[@]} else if [ ${#arr[@]} == 4 ]; then xml="$xml<checkresult type='service' checktype='$checktype'> <servicename>${arr[1]}</servicename> <hostname>${arr[0]}</hostname> <state>${arr[2]}</state> <output>${arr[3]}</output>" else xml="$xml<checkresult type='host' checktype='$checktype'> <hostname>${arr[0]}</hostname> <state>${arr[1]}</state> <output>${arr[2]}</output>" fi xml="$xml</checkresult>" checkcount=$[checkcount+1] fi fi done IFS=" " fi if [[ -n $file ]]; then xml=$(<"$file") send_data "$xml" fi if [[ -n $directory ]]; then #echo "Processing directory..." for f in "$directory"/* do #echo "Processing $f file..." # take action on each file. $f store current file name xml=$(<"$f") send_data "$xml" "$directory/$f" done fi if [[ -z $file && -z $directory ]]; then xml="<?xml version='1.0'?> <checkresults> $xml </checkresults>" send_data "$xml" echo "Sent $checkcount checks to $url" fi
The basic usage of the command is;
/opt/clients/send_nrdp.sh -u API_URL -t TOKENConfigure Global Host and Service Event Handlers on Remote Nagios Server
On the remote Nagios server, you need to configure Global Host and Service Event Handlers. The define the commands (in this case the NRDP clients scripts) that are executed for every host or service state change.
So in this case, you have to define two scripts that submits host check and service check results to central Nagios server.
Thus, open Nagios configuration file, nagios.cfg and set the appropriate command names for the options below;
- global_host_event_handler
- global_service_event_handler
vim /usr/local/nagios/etc/nagios.cfg# GLOBAL HOST AND SERVICE EVENT HANDLERS
...
global_host_event_handler=global_host_send_nrdp
global_service_event_handler=global_service_send_nrdp
...Save and exit the file;
In the above config, global_host_send_nrdp and global_service_send_nrdp are names of the commands for submitting host and service check results to the NRDP server on the central Nagios server.
Next, define the specific commands to submit the host checks and service checks;
vim /usr/local/nagios/etc/objects/commands.cfgdefine command {
command_name global_host_send_nrdp
command_line /usr/bin/echo -e "$HOSTNAME$\t$HOSTSTATEID$\t$HOSTOUTPUT$\n" | /usr/local/nrdp/clients/send_nrdp.sh -u http://192.168.57.48/nrdp/ -t 90dfs7jwn3
}
define command {
command_name global_service_send_nrdp
command_line /usr/bin/echo -e "$HOSTNAME$\t$SERVICEDESC$\t$SERVICESTATEID$\t$SERVICEOUTPUT$\n" | /usr/local/nrdp/clients/send_nrdp.sh -u http://192.168.57.48/nrdp/ -t 90dfs7jwn3
}
The token used must match the token defined on the NRDP API.
The host check command will submit;
- $HOSTNAME$ as defined by the host_name under host definition
- $HOSTSTATEID$: A number that corresponds to the current state of the host: 0=UP, 1=DOWN, 2=UNREACHABLE.
- $HOSTOUTPUT$: The first line of text output from the last host check (i.e. “Ping OK”).
The service check command will submit;
- $HOSTNAME$ as defined by the host_name under host definition
- $SERVICEDESC$: The long name/description of the service (i.e. “Main Website”). This value is taken from the service_description directive of the service definition.
- $SERVICESTATEID$: A number that corresponds to the current state of the service: 0=OK, 1=WARNING, 2=CRITICAL, 3=UNKNOWN.
- $SERVICEOUTPUT$: The first line of text output from the last service check (i.e. “Ping OK”).
Once that is done, check Nagios for any configuration error;
/usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfgIf there is no error;
Total Warnings: 0
Total Errors: 0Restart it;
systemctl stop nagiossystemctl start nagiosConfirm and verify Nagios passive checks on Central Nagios server
When the Host/Service state changes on the remote Nagios, the result is submitted to the central Nagios server.
You can manually test host state changes;
/usr/bin/echo -e "mongo\t0\tUP\n" | /usr/local/nrdp/clients/send_nrdp.sh -u http://192.168.57.48/nrdp/ -t 90dfs7jwn3To manually test a service;
/usr/bin/echo -e "mongo\t0\tCurrent Load\tOK\n" | /usr/local/nrdp/clients/send_nrdp.sh -u http://192.168.57.48/nrdp/ -t 90dfs7jwn3The result should be reflected on the central Nagios server;
For the purposes of testing with Nagios, on the remote host, I will change the IP address of the host, mongo to an unreachable IP and restart Nagios.
When Nagios tries to check the host and finds that it is unreachable, the state will be submitted to the central Nagios server;
These are sample logs on remote nagios;
tail -f /usr/local/nagios/var/nagios.log[1663377877] SERVICE ALERT: mongo;Root Partition;CRITICAL;SOFT;1;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663377877] GLOBAL SERVICE EVENT HANDLER: mongo;Root Partition;CRITICAL;SOFT;1;global_service_send_nrdp [1663377881] HOST ALERT: mongo;DOWN;SOFT;1;CRITICAL - Host Unreachable (192.168.56.44) [1663377881] GLOBAL HOST EVENT HANDLER: mongo;DOWN;SOFT;1;global_host_send_nrdp [1663377922] SERVICE ALERT: mongo;Swap Usage;CRITICAL;HARD;1;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663377922] GLOBAL SERVICE EVENT HANDLER: mongo;Swap Usage;CRITICAL;HARD;1;global_service_send_nrdp [1663377941] SERVICE ALERT: mongo;Root Partition;CRITICAL;HARD;4;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663377941] GLOBAL SERVICE EVENT HANDLER: mongo;Root Partition;CRITICAL;HARD;4;global_service_send_nrdp [1663377944] HOST ALERT: mongo;DOWN;SOFT;2;CRITICAL - Host Unreachable (192.168.56.44) [1663377944] GLOBAL HOST EVENT HANDLER: mongo;DOWN;SOFT;2;global_host_send_nrdp [1663377968] SERVICE ALERT: mongo;Current Users;CRITICAL;HARD;1;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663377968] GLOBAL SERVICE EVENT HANDLER: mongo;Current Users;CRITICAL;HARD;1;global_service_send_nrdp [1663377968] SERVICE ALERT: mongo;Total Processes;CRITICAL;HARD;1;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663377968] GLOBAL SERVICE EVENT HANDLER: mongo;Total Processes;CRITICAL;HARD;1;global_service_send_nrdp [1663378007] HOST ALERT: mongo;DOWN;SOFT;3;CRITICAL - Host Unreachable (192.168.56.44) [1663378007] GLOBAL HOST EVENT HANDLER: mongo;DOWN;SOFT;3;global_host_send_nrdp [1663378007] SERVICE ALERT: mongo;PING;CRITICAL;HARD;1;CRITICAL - Host Unreachable (192.168.56.44) [1663378007] GLOBAL SERVICE EVENT HANDLER: mongo;PING;CRITICAL;HARD;1;global_service_send_nrdp [1663378020] SERVICE ALERT: mongo;Current Load;CRITICAL;HARD;1;(No output on stdout) stderr: connect to address 192.168.56.44 port 5666: No route to host [1663378020] GLOBAL SERVICE EVENT HANDLER: mongo;Current Load;CRITICAL;HARD;1;global_service_send_nrdp ...
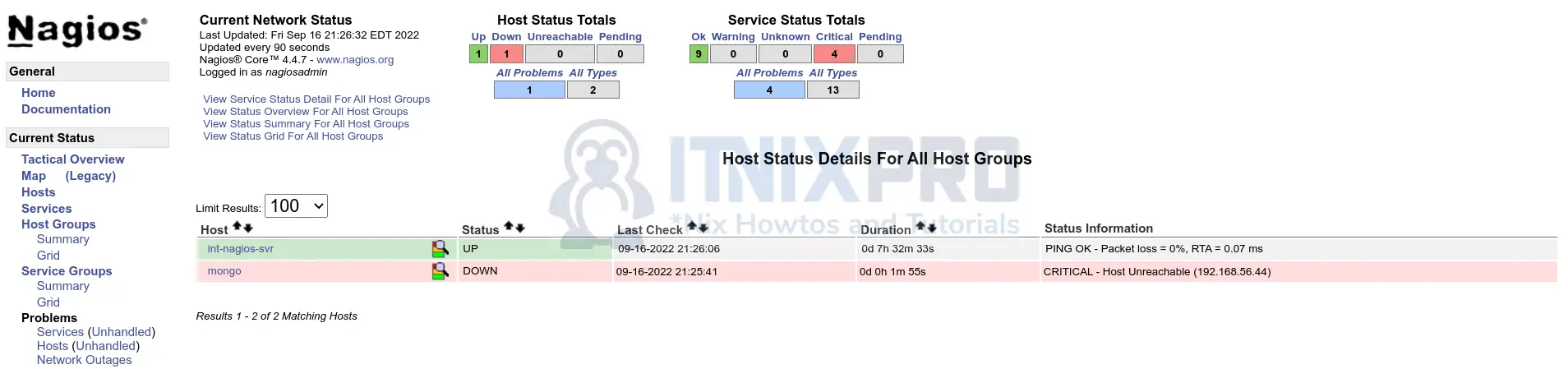
When you check on the central Nagios, the state of the host has also changed;
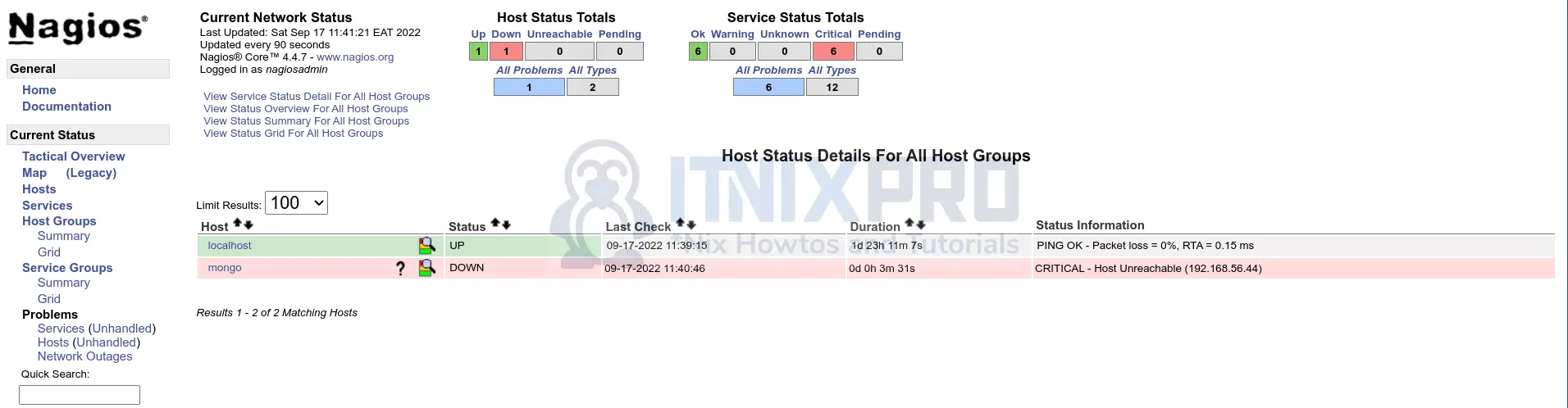
Put back the correct host IP on the remote host and restart Nagios and tail the logs;
tail -f /usr/local/nagios/var/nagios.logAs the host and services recover on the remote Nagios server;
[1663378198] HOST ALERT: mongo;UP;SOFT;1;PING OK - Packet loss = 0%, RTA = 1.26 ms [1663378198] GLOBAL HOST EVENT HANDLER: mongo;UP;SOFT;1;global_host_send_nrdp [1663378219] SERVICE FLAPPING ALERT: mongo;Swap Usage;STARTED; Service appears to have started flapping (23.6% change >= 20.0% threshold) [1663378219] SERVICE ALERT: mongo;Swap Usage;OK;HARD;4;SWAP OK - 100% free (2047 MB out of 2047 MB) [1663378219] GLOBAL SERVICE EVENT HANDLER: mongo;Swap Usage;OK;HARD;4;global_service_send_nrdp [1663378237] SERVICE ALERT: mongo;Root Partition;OK;HARD;4;DISK OK - free space: / 15637 MiB (89.90% inode=99%): [1663378237] GLOBAL SERVICE EVENT HANDLER: mongo;Root Partition;OK;HARD;4;global_service_send_nrdp
The same will be reflected on the central Nagios server;
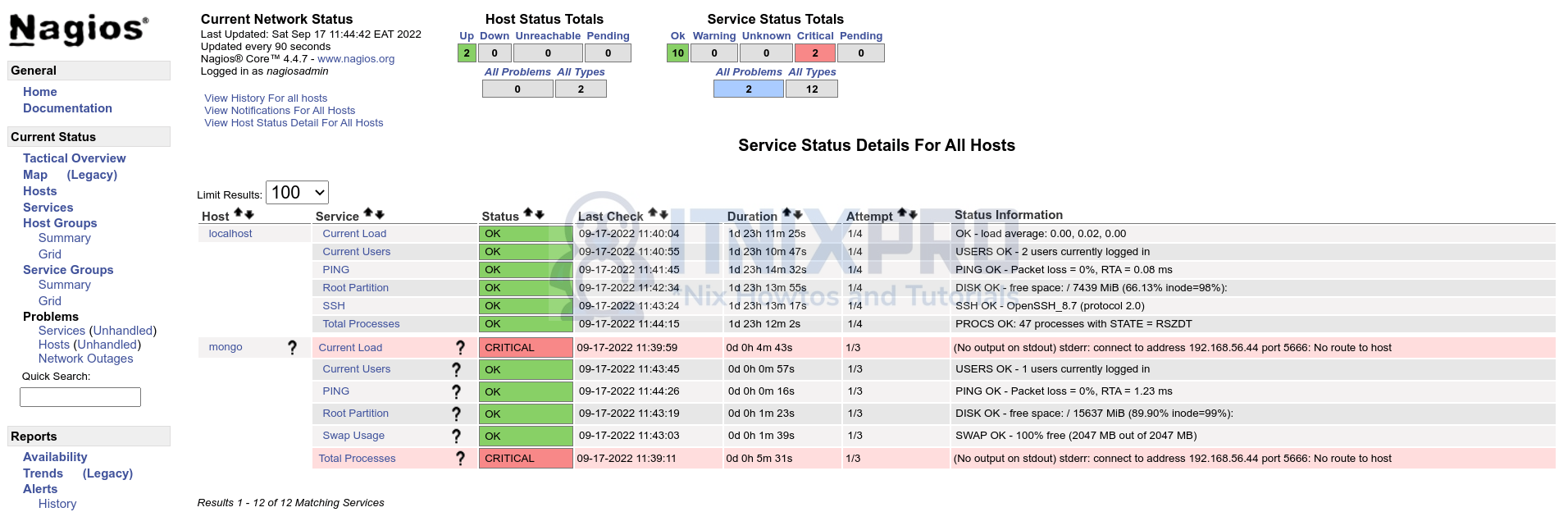
And that is all it takes to setup Nagios Passive Checks with NRDP.
