This article will go through how to install OpenSCAP on Rocky Linux. The auditing tool OpenSCAP uses the XCCDF (Extensible Configuration Checklist Description Format) to define security checklists, a standard for conveying checklist content. Additionally, it connects with additional specifications like CPE, CCE, and OVAL to produce a SCAP-expressed checklist that SCAP-validated products can process.
How to Install OpenSCAP on Rocky Linux
- Update your system packages using the command below.
sudo dnf update- Then install OpenSCAP and SCAP security guide using the following command.
sudo dnf install openscap-scanner scap-security-guideSample output
Dependencies resolved. ===================================================================== Package Arch Version Repo Size ===================================================================== Installing: openscap-scanner x86_64 1:1.3.6-3.el9.rocky.0.1 appstream 63 k scap-security-guide noarch 0.1.60-6.el9_0.rocky.0.3 appstream 1.2 M Installing dependencies: openscap x86_64 1:1.3.6-3.el9.rocky.0.1 appstream 1.9 M Transaction Summary ===================================================================== Install 3 Packages Total download size: 3.2 M Installed size: 119 M Is this ok [y/N]: y Downloading Packages: (1/3): openscap-scanner-1.3.6-3.el9. 16 kB/s | 63 kB 00:03 (2/3): scap-security-guide-0.1.60-6. 102 kB/s | 1.2 MB 00:12 (3/3): openscap-1.3.6-3.el9.rocky.0. 121 kB/s | 1.9 MB 00:15 --------------------------------------------------------------------- Total 171 kB/s | 3.2 MB 00:18 Running transaction check Transaction check succeeded. Running transaction test Transaction test succeeded. Running transaction Preparing : 1/1 Installing : openscap-1:1.3.6-3.el9.rocky.0.1.x86_64 1/3 Installing : openscap-scanner-1:1.3.6-3.el9.rocky.0.1. 2/3 Installing : scap-security-guide-0.1.60-6.el9_0.rocky. 3/3 Running scriptlet: scap-security-guide-0.1.60-6.el9_0.rocky. 3/3 Verifying : openscap-scanner-1:1.3.6-3.el9.rocky.0.1. 1/3 Verifying : openscap-1:1.3.6-3.el9.rocky.0.1.x86_64 2/3 Verifying : scap-security-guide-0.1.60-6.el9_0.rocky. 3/3 Installed: openscap-1:1.3.6-3.el9.rocky.0.1.x86_64 openscap-scanner-1:1.3.6-3.el9.rocky.0.1.x86_64 scap-security-guide-0.1.60-6.el9_0.rocky.0.3.noarch Complete!
- The SCAP security guide will be in the
/usr/share/xml/scap/ssg/contentdirectory after the installation. You can list it using the command below.
ls /usr/share/xml/scap/ssg/content/Sample output
ssg-rhel9-ds.xml ssg-rl9-ds.xml- To view the description run the following command with the guide name at the end e.g.
ssg-rhel9-ds.xmlorssg-rl9-ds.xml
oscap info /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xmlSample output
Document type: Source Data Stream
Imported: 2022-06-28T00:17:14
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf-1.2.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-xccdf-1.2.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2' file which is referenced from datastream
Status: draft
Generated: 2022-06-27
Resolved: true
Profiles:
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediary
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2
Title: [DRAFT] Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171)
Id: xccdf_org.ssgproject.content_profile_cui
Title: Australian Cyber Security Centre (ACSC) Essential Eight
Id: xccdf_org.ssgproject.content_profile_e8
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Title: Australian Cyber Security Centre (ACSC) ISM Official
Id: xccdf_org.ssgproject.content_profile_ism_o
Title: [DRAFT] Protection Profile for General Purpose Operating Systems
Id: xccdf_org.ssgproject.content_profile_ospp
Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_pci-dss
Title: [DRAFT] DISA STIG for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig
Title: [DRAFT] DISA STIG with GUI for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig_gui
Referenced check files:
ssg-rhel9-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel9-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-ocil.xml
Ref-Id: scap_org.open-scap_cref_--builddir--build--BUILD--scap-security-guide-0.1.60--build--ssg-rhel9-cpe-oval.xml
Ref-Id: scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2
Dictionaries:
Ref-Id: scap_org.open-scap_cref_--builddir--build--BUILD--scap-security-guide-0.1.60--build--ssg-rhel9-cpe-dictionary.xml
- Next, scan Rocky Linux for any vulnerabilities, enter the profile and content to perform an audit.
oscap xccdf eval \
--profile xccdf_org.ssgproject.content_profile_ospp \
--results ssg-rhel9-ds.xml \
--report ssg-rhel9-ds.html \
--fetch-remote-resources \
/usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xmlSample output
Downloading: https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2 ... ok --- Starting Evaluation --- Title Install AIDE Rule xccdf_org.ssgproject.content_rule_package_aide_installed Ident CCE-90843-4 Result notapplicable Title Enable Dracut FIPS Module Rule xccdf_org.ssgproject.content_rule_enable_dracut_fips_module Ident CCE-86547-7 Result notapplicable Title Enable FIPS Mode Rule xccdf_org.ssgproject.content_rule_enable_fips_mode Ident CCE-88742-2 Result notapplicable Title Install crypto-policies package Rule xccdf_org.ssgproject.content_rule_package_crypto-policies_installed Ident CCE-83442-4 Result notapplicable Title Configure BIND to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_bind_crypto_policy Ident CCE-83451-5 Result notapplicable Title Configure System Cryptography Policy Rule xccdf_org.ssgproject.content_rule_configure_crypto_policy Ident CCE-83450-7 Result notapplicable Title Configure Kerberos to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_kerberos_crypto_policy Ident CCE-83449-9 Result notapplicable Title Configure Libreswan to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_libreswan_crypto_policy Ident CCE-83446-5 Result notapplicable Title Configure OpenSSL library to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_openssl_crypto_policy Ident CCE-83452-3 Result notapplicable Title Configure SSH to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_ssh_crypto_policy Ident CCE-83445-7 Result notapplicable Title Ensure /home Located On Separate Partition Rule xccdf_org.ssgproject.content_rule_partition_for_home Ident CCE-83468-9 Result notapplicable Title Ensure /var Located On Separate Partition Rule xccdf_org.ssgproject.content_rule_partition_for_var Ident CCE-83466-3 Result notapplicable Title Ensure /var/log Located On Separate Partition Rule xccdf_org.ssgproject.content_rule_partition_for_var_log Ident CCE-90848-3 Result notapplicable Title Ensure /var/log/audit Located On Separate Partition Rule xccdf_org.ssgproject.content_rule_partition_for_var_log_audit Ident CCE-90847-5 Result notapplicable Title Ensure /var/tmp Located On Separate Partition Rule xccdf_org.ssgproject.content_rule_partition_for_var_tmp Ident CCE-83487-9 Result notapplicable Title Install sudo Package Rule xccdf_org.ssgproject.content_rule_package_sudo_installed Ident CCE-83523-1 Result notapplicable Title Ensure gnutls-utils is installed Rule xccdf_org.ssgproject.content_rule_package_gnutls-utils_installed Ident CCE-83494-5 Result notapplicable Title Install openscap-scanner Package Rule xccdf_org.ssgproject.content_rule_package_openscap-scanner_installed Ident CCE-83502-5 Result notapplicable Title Install scap-security-guide Package Rule xccdf_org.ssgproject.content_rule_package_scap-security-guide_installed Ident CCE-83505-8 Result notapplicable Title Install subscription-manager Package Rule xccdf_org.ssgproject.content_rule_package_subscription-manager_installed Ident CCE-83506-6 Result notapplicable Title Uninstall gssproxy Package Rule xccdf_org.ssgproject.content_rule_package_gssproxy_removed Ident CCE-83516-5 Result notapplicable Title Uninstall iprutils Package Rule xccdf_org.ssgproject.content_rule_package_iprutils_removed Ident CCE-83519-9 Result notapplicable Title Uninstall krb5-workstation Package Rule xccdf_org.ssgproject.content_rule_package_krb5-workstation_removed Ident CCE-83520-7 Result notapplicable Title Install dnf-automatic Package Rule xccdf_org.ssgproject.content_rule_package_dnf-automatic_installed Ident CCE-83454-9 Result notapplicable Title Configure dnf-automatic to Install Available Updates Automatically Rule xccdf_org.ssgproject.content_rule_dnf-automatic_apply_updates Ident CCE-83456-4 Result notapplicable Title Configure dnf-automatic to Install Only Security Updates Rule xccdf_org.ssgproject.content_rule_dnf-automatic_security_updates_only Ident CCE-83461-4 Result notapplicable Title Ensure gpgcheck Enabled In Main dnf Configuration Rule xccdf_org.ssgproject.content_rule_ensure_gpgcheck_globally_activated Ident CCE-83457-2 Result notapplicable Title Ensure gpgcheck Enabled for Local Packages Rule xccdf_org.ssgproject.content_rule_ensure_gpgcheck_local_packages Ident CCE-83463-0 Result notapplicable
- After scanning, you will get your system report generated in HTML in the home directory as specified in the
oscapcommand above, double click to open it in the browser. Sample OpenSCAP Evaluation Report.
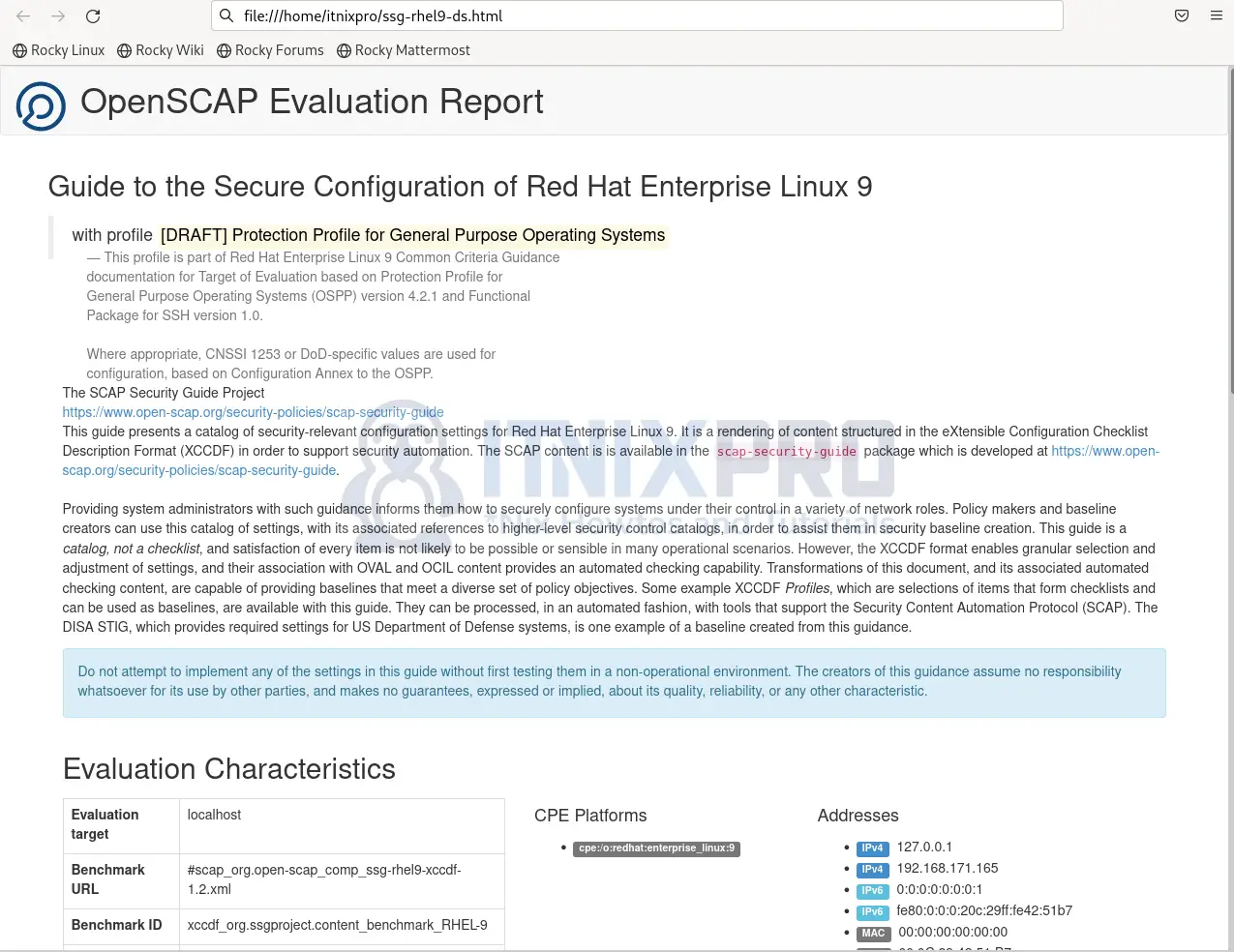
- Under Compliance and Scoring, you will find recommendations for your system.
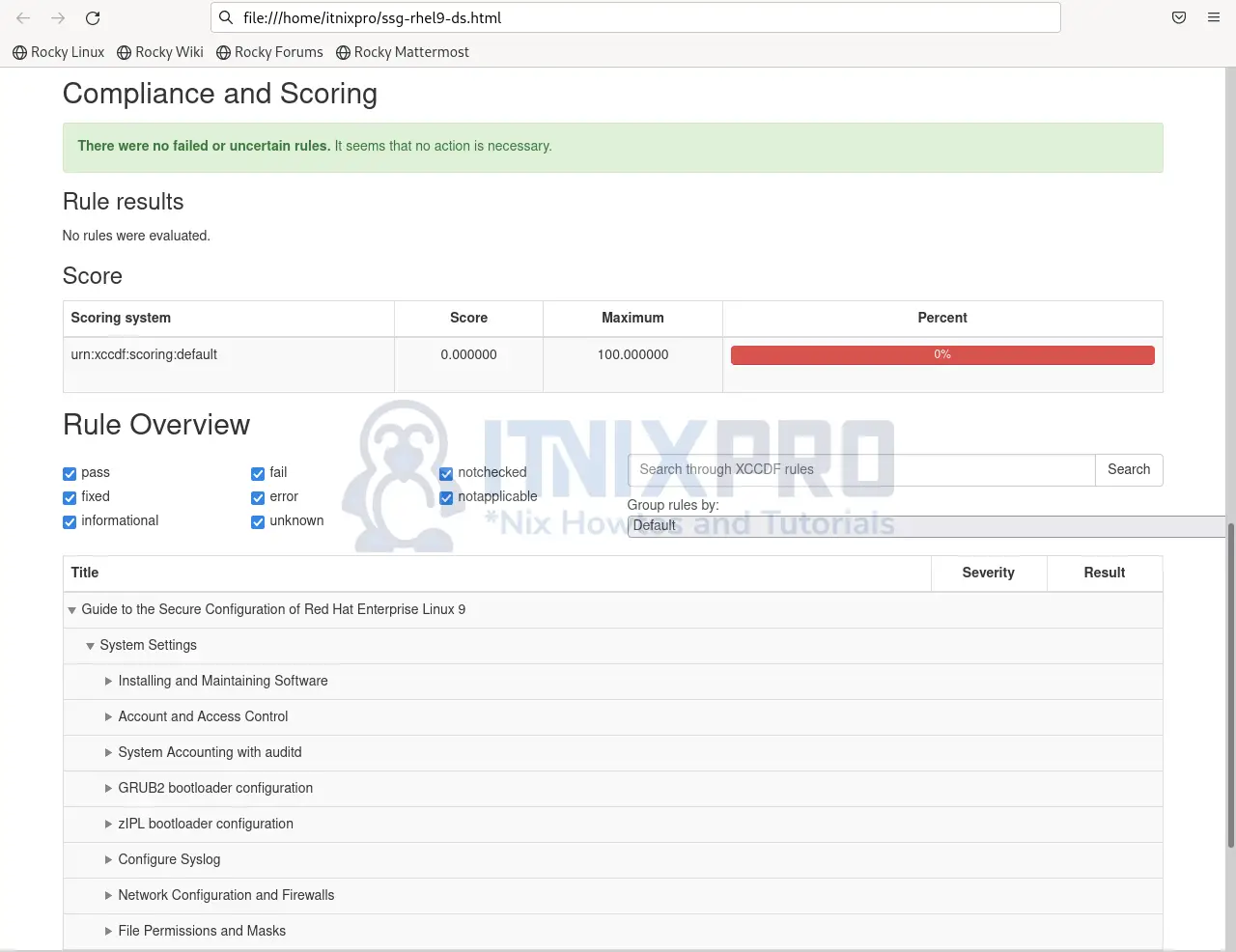
- You can click to view more on a specific category.
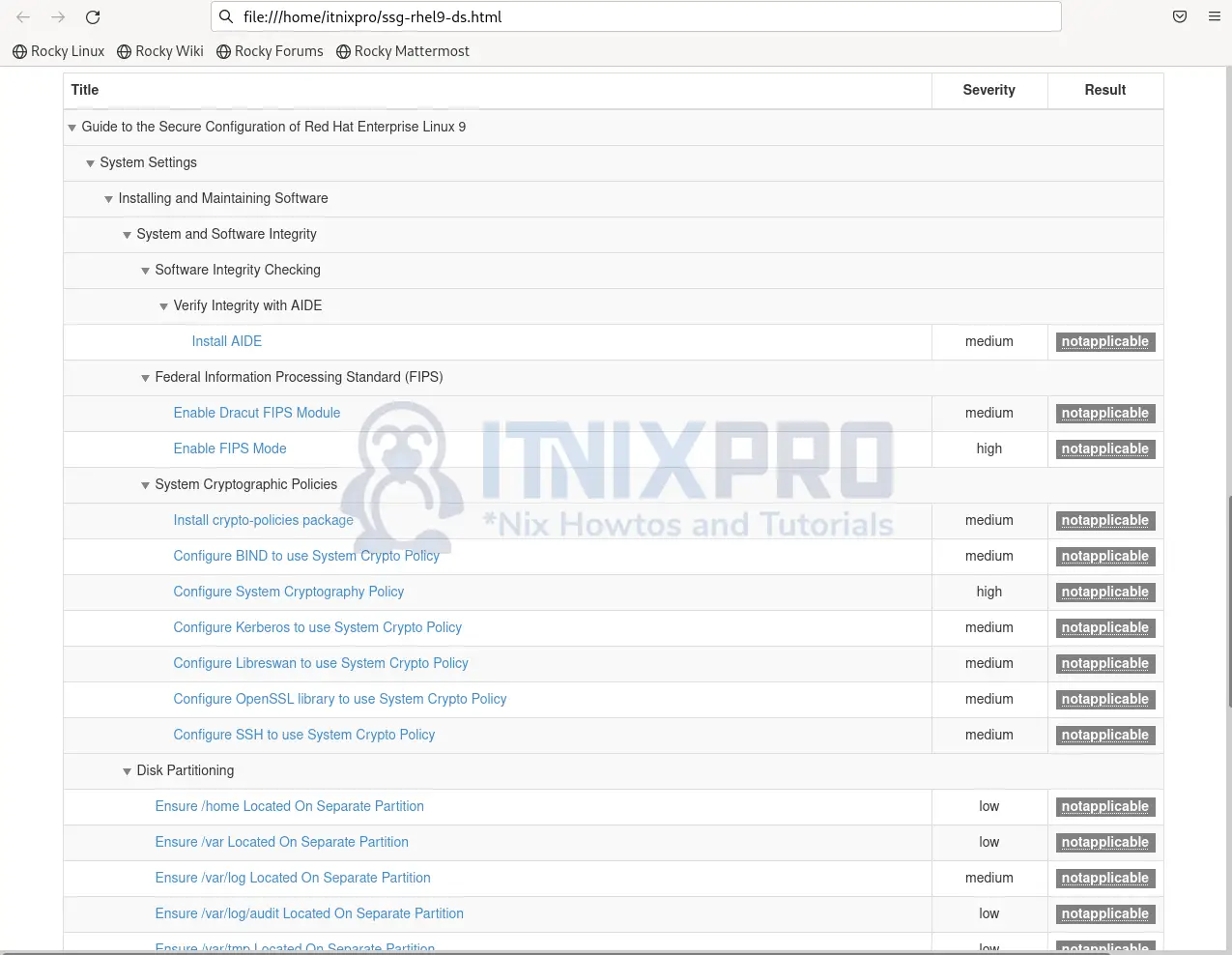
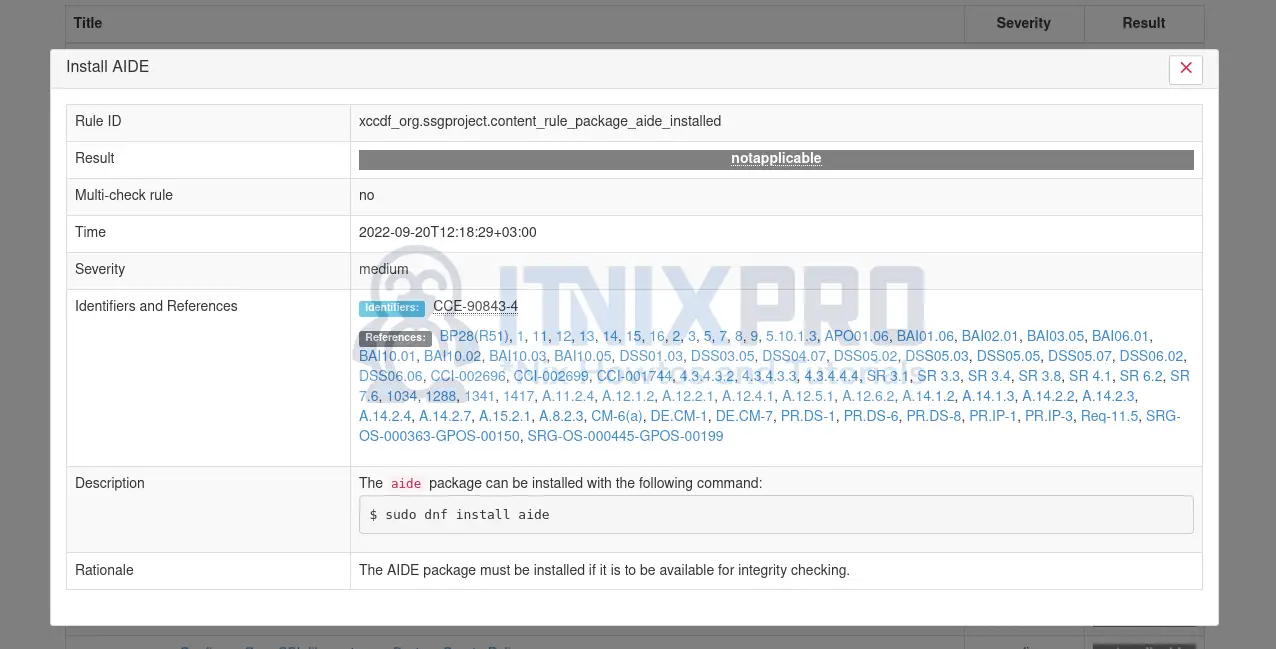
- Details about specific results.
- You have made it to the end of our article, we have gone through how to install OpenSCAP on Rocky Linux.
Read more on OpenSCAP Documentation
Other Tutorials
Setup Nagios Passive Checks with NRDP

Thank you